增加开发及常用文档英文翻译
|
|
@ -0,0 +1,31 @@
|
|||
# <center>How to add boot parameters to grub</center>
|
||||
#### <center>Author: OK</center>
|
||||
#### <center>2022-04-22 23:36:00</center>
|
||||
|
||||
|
||||
|
||||
## How to add boot parameters to grub
|
||||
For grub2, ubuntu gives an official configuration file /etc/default/grub. Most of the grub2 settings can be done in this file, and the structure of this file is relatively simple and easy to modify. There is no need to change /boot/grub/grub.cfg or /etc/grub.d/ directly.
|
||||
|
||||
Modifying /etc/default/grub requires only one simple command.
|
||||
sudo vim /etc/default/grub
|
||||
|
||||
The following are the system defaults and the most common ways to modify the menu display time and default operating system.
|
||||
#If you change this file, run 'update-grub' afterwards to update
|
||||
#/boot/grub/grub.cfg.
|
||||
|
||||
GRUB_DEFAULT=0 #Changing 0 to saved allows grub to remember which system was selected the last time it booted
|
||||
GRUB_HIDDEN_TIMEOUT=0
|
||||
GRUB_HIDDEN_TIMEOUT_QUIET=true
|
||||
GRUB_TIMEOUT="5" #Show the time to start the selection menu
|
||||
GRUB_DISTRIBUTOR=`lsb_release -i -s 2> /dev/null || echo Debian`
|
||||
GRUB_CMDLINE_LINUX_DEFAULT="quiet splash"
|
||||
GRUB_CMDLINE_LINUX=""
|
||||
|
||||
After the modification is complete, execute the following command.
|
||||
|
||||
$ sudo apt-get install grub2-common //If you don't have the update-grub command, run this installation command first
|
||||
|
||||
$ sudo update-grub //Generate the grub configuration file
|
||||
|
||||
That's all.
|
||||
|
|
@ -0,0 +1,38 @@
|
|||
# <center>Basic ssh usage</center>
|
||||
#### <center>Author: OK</center>
|
||||
#### <center>2022-04-22 23:36:00</center>
|
||||
|
||||
|
||||
1. SSH is the abbreviation of Secure Shell, developed by the Network Working Group of IETF; SSH is a security protocol based on the application layer, generally speaking, it is most frequently used to log in to remote hosts, it has a built-in sftp module that uses encrypted transmission, and the port used is 22, which is much more secure than The security of sftp is much better than that of ftp without encryption. The simplest command format is as follows:
|
||||
`ssh Username@host`
|
||||
|
||||
Of course this is based on the default port, if the sshserver port is not the default, it will look like this:
|
||||
`ssh Username@host -p port`
|
||||
Then you will be prompted to enter a password, the password is the password of the user name you want to log in, the user must exist, and is allowed to log in only, in general, we install the system when the establishment of the user is no problem, and the default password does not return to show.
|
||||
|
||||
He can also proxy x11 protocol, transfer the interface to the local, but actually run in the remote host, but the remote host needs to install xauth, and, both local and remote start x11 proxy to be able to, the actual test some applications may not be supported, in addition, if the local system is win, it may not work well, if it is linux then as long as the network speed is enough or The disadvantage is that you may not be able to use Chinese input method, you can only copy and paste, although you can configure the way to let the input method start, but I have not succeeded. In addition, there is a port mapping role, generally speaking, called ssh tunneling, you can map the remote port to the local, you can also map the local port to the remote, but also can be changed to a two-way, so that you can be used as an intranet penetration, or local services exposed to the remote, you can also turn the remote port into local access, and is encrypted with ssh do not worry about being eavesdropped, etc., generally In general, the development will be used more, the database port mapping to a local port, direct access, without opening the corresponding port of the public network to improve security, and then for example, vnc, the vnc port mapping to the local, although vncview prompt not encrypted, but the data transmitted in the middle is ssh encrypted, do not worry about being eavesdropped, and can close the corresponding port firewall ssh can disable password login and only use key login, or both, as long as there is a public key and private key, and then put the public key into a specific file, you can directly use the private key to login without encryption.
|
||||
|
||||
2. SSh a little trick, ssh if in a period of time does not respond then you can modify the heartbeat time, every certain time to send an empty packet, keep the response, in general I do not recommend setting the time more than 30, if the network environment is almost 30 may be broken, generally set to 15, extreme cases set to 5, here in seconds.
|
||||
There is also the fact that if you exit the ssh, then the running program will be killed, you can use the screen command to let the program run in the background, and then Ctrl + a + d to return, so you can exit the ssh without worrying about the program hanging, the recovery command is also available.
|
||||
|
||||
3. If it's the first time you log into a host a prompt will appear, something like the following.
|
||||
|
||||
This is the first time you log into a new host to give the prompt, as to why this prompt, because the ssh communication process leads to, is a kind of verification method, specific you can check the Baidu, it should be noted that here only enter yes to continue, simply a y or enter is not allowed, then enter the password to log in, after successful login will display some welcome message, and the last login address.
|
||||
Then enter the password to log in, after successful login will display some welcome message, and the last login address.
|
||||
|
||||
The bottom one looks the same as the top one, but it is actually the result of ssh login, because the terminal is displayed in the format of "username@hostname".
|
||||
Once you have successfully logged in, you can use the terminal to execute some commands on the remote host
|
||||
|
||||
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~Gorgeous divider~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
|
||||
This is because ssh is divided into two parts, one is the server and the other is the client, the client is the ssh command we used above, the server part is not necessarily available in the desktop environment, the server version of Ubuntu will let the user choose whether to install the server or not during the installation. If not, you can directly install openssh-server, it should be noted that the default server we installed prohibits root user login, so to allow root users to log in remotely you need to modify the configuration file of the server, again without going into detail, a tutorial online to save resources.
|
||||
|
||||
|
||||
|
||||
The following articles were referenced in the writing of this article.
|
||||
[https://forum.openkylin.top/forum.php?mod=viewthread&tid=193097](https://forum.openkylin.top/forum.php?mod=viewthread&tid=193097)
|
||||
[https://forum.openkylin.top/forum.php?mod=viewthread&tid=193211](https://forum.openkylin.top/forum.php?mod=viewthread&tid=193211)
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
|
|
@ -0,0 +1,246 @@
|
|||
|
||||
# <center>Using KVM Virtual Machines</center>
|
||||
#### <center>Author:ymz316</center>
|
||||
#### <center>2022-05-12 17:50:00</center>
|
||||
<br>
|
||||
|
||||
KVM (Kernel-based Virtual Machine) is a kernel-based (kernel built-in) virtual machine. It is generally used by QEMU to complete the creation of virtual machines, and the suffix name of the virtual machine image is mostly qcow2.
|
||||
|
||||
Notes before installing a KVM virtual machine.
|
||||
|
||||
>1. KVM itself does not emulate any hardware devices, it uses virtualization capabilities provided by hardware such as (Intel VT-x, AMD-V, ARM virtualization extensions, etc.), so KVM **requires chip support and enables virtualization technology** (Intel's VT extensions or AMD's AMD-V extensions).
|
||||
>2. KVM requires QEMU to work with hardware devices such as motherboard, memory and I/O emulation, and also **requires the installation of some management software packages** for the purpose of rapid virtual machine creation.
|
||||
>3. Virtual machine installation requires the use of a network, so you need to first **configure network information** to provide network device support for the virtual machine installation.
|
||||
>4. Once the above is ready, you can **create a virtual machine**.
|
||||
|
||||
### I. Prerequisites for KVM installation
|
||||
|
||||
**1) Verify support for hardware virtualization (Intel's VT extensions or AMD's AMD-V extensions)**
|
||||
|
||||
```
|
||||
$ LC_ALL=C lscpu | grep Virtualization
|
||||
Virtualization: VT-x
|
||||
```
|
||||
Or:
|
||||
```
|
||||
$ grep -Eoc '(vmx|svm)' /proc/cpuinfo #或者 egrep -c '(vmx|svm)' /proc/cpuinfo
|
||||
16
|
||||
```
|
||||
|
||||
If a number greater than zero is output (i.e., the number of CPU cores), the CPU supports hardware virtualization; if 0 is output, the CPU does not support hardware virtualization, try rebooting into the BIOS settings to enable VT technology.
|
||||
|
||||
Note: The $ here is the terminal prompt and does not need to be copied
|
||||
|
||||
**2)Determine if the server is capable of running hardware-accelerated KVM virtual machines**
|
||||
|
||||
```
|
||||
$ kvm-ok #If prompted for this command, install it by sudo apt install cpu-checker
|
||||
INFO: /dev/kvm exists
|
||||
KVM acceleration can be used
|
||||
```
|
||||
|
||||
Note: The $ here is the terminal prompt and does not need to be copied
|
||||
|
||||
### II. Install the KVM virtualization management package
|
||||
|
||||
**KVM Related virtualization management packages**
|
||||
|
||||
>**qemu-kvm** :This package is required for 20.04, but it seems to be integrated in 22.04 and does not need to be installed.
|
||||
**libvirt**:A collection of software to manage virtual machines and other virtualization functions (e.g. storage management, network management). It includes an API library, a daemon (libvirtd) and a command line tool (virsh). It provides a common API for common functions implemented by supported virtual machine monitors. libvirt's main goal is to provide a unified and reliable set of APIs for various virtualization tools, allowing the upper layers to manage multiple different virtualization technologies in a single way, including KVM, vmware, XEN, Hyper-v, LXC and other hypervisors. Hypervisor requires the installation of the **libvirt-daemon-system** package to use the libvirt daemon as a configuration file for running system services.
|
||||
**libvirt-clients** :This package is used to manage the software of the virtualization platform and is usually installed automatically when libvirt-daemon-system is installed.
|
||||
**virt-manager** :libvirt-based GUI tools (graphical user interface).
|
||||
**virtinst** :A set of command line tools for creating virtual machines. Normally, this package is automatically installed when virt-manager is installed.
|
||||
**bridge-utils** :Command line tool for configuring Ethernet bridges.
|
||||
**ovmf**:The UEFI firmware for the virtual machine is installed so that the virtual machine system can boot from uefi.
|
||||
|
||||
The installation command is:
|
||||
|
||||
```
|
||||
sudo apt install qemu qemu-kvm libvirt-daemon-system virt-manager bridge-utils ovmf
|
||||
```
|
||||
|
||||
### III. Client network configuration
|
||||
|
||||
After the client is installed, you need to set up a network interface for it to communicate with the host network and the network between the clients. The linux system needs to use the network communication when it is installed, so you have to set up the network connection for the client in advance.
|
||||
|
||||
KVM There are two ways to connect to the client network.
|
||||
|
||||
- **User Networking**: Also known as the NAT method. A simple way to allow virtual machines to access resources on the host, Internet or local network, but they cannot be accessed from the network or other clients, and performance requires major tuning.
|
||||
- **Virtual Bridge**: Also known as the Bridge approach, the Bridge approach allows a virtual machine to become a host with a separate IP on the network, so clients and machines inside the subnet can communicate with each other. This method is a little more complicated than the user network, but it is easy to communicate between the client and the Internet and between the client and the host after setup.
|
||||
|
||||
To learn about NAT as an example.
|
||||
|
||||
Type `sudo virt-manager` in the terminal or click on `Virtual System Manager` in the start menu to open the virt-manager GUI.
|
||||
|
||||

|
||||
|
||||
Click "Edit" - "Connection Details" to enter the network configuration interface, and select the virtual network, where by default there is a default NAT network connection, the device name is virbr0, the network segment is 192.168.122.0/24.
|
||||
|
||||

|
||||
|
||||
|
||||
You can click the plus sign below to create a new network connection, here we create a network connection named network, forward to select "any physical device" (will create a network card device virbr1), network segment for 192.168.100.0/24, set up DHCP, click Finish to configure successfully. The next step in the virtual machine installation process can be set to this network connection method.
|
||||
|
||||

|
||||
|
||||
|
||||
### IV. Customer Virtual Machine Installation
|
||||
|
||||
Virtual machine installation can be done through virt-manager graphical tool or through qemu-img command.
|
||||
|
||||
**1. virt-manager graphical tool installation**
|
||||
|
||||
Open the virt-manager GUI by typing `sudo virt-manager` in the terminal or clicking on `Virtual System Manager` in the start menu.
|
||||
|
||||

|
||||
|
||||
|
||||
1) Click "File" - "Create Virtual Machine", or click the Create Virtual Machine icon, then select the local installation media and click Forward.
|
||||
|
||||
>Note: If we have already copied a disk image of the virtual machine online or elsewhere with the system already installed, you can select "Import existing disk image".
|
||||
|
||||

|
||||
|
||||
2) Select the installation source (ISO) and virtual machine system format (such as red hat Linux 8 or something like that) and click forward
|
||||
|
||||

|
||||
|
||||
3) Enter the virtual machine memory, the number of cpu cores (can not be greater than the number of host cores), click forward
|
||||
|
||||

|
||||
|
||||
4) Select the disk image (virtual machine installation should also have a virtual disk, right), here we create a 40G disk, click forward
|
||||
|
||||
> Note: The default disk image path here is /var/lib/libirt/images/*.qcow2, while if we need to use an already created disk image or need to customize the storage location of the disk image, you can select "Select or create custom storage"
|
||||
|
||||

|
||||
|
||||
5) Enter the virtual machine instance name, select the network, and click Forward.
|
||||
|
||||
> If you don't know how to choose a network, you may want to brush up on your knowledge of several modes of virtual machine networking (NAT, bridge, only_host).
|
||||
|
||||

|
||||
|
||||
6) At this point, it is time to enter the installation of the virtual machine system
|
||||
|
||||

|
||||
|
||||
If you are prompted with the error "Error connecting to graphics console: Error opening Spice console, SpiceClientGtk missing", you can try the following command to solve it.
|
||||
|
||||
```
|
||||
hollowman@hollowman-F117:~$ apt search SpiceClientGtk
|
||||
Sorting... Done
|
||||
Full text search... Done
|
||||
gir1.2-spiceclientgtk-3.0/focal 0.37-2fakesync1 amd64
|
||||
GTK3 widget for SPICE clients (GObject-Introspection)
|
||||
|
||||
hollowman@hollowman-F117:~$ sudo apt install gir1.2-spiceclientgtk-3.0
|
||||
```
|
||||
**2. Command installation**
|
||||
|
||||
**1) Create a virtual machine disk image**
|
||||
|
||||
```
|
||||
$ qemu-img create -f qcow2 diskname.qcow2 40G
|
||||
$ ll -h diskname.qcow2 #Check the size of the image on the host system, although there is 40G disk, but because there is no data, it actually occupies only 196K
|
||||
-rwxrwxrwx 1 hollowman hollowman 196K November 24 13:30 diskname.qcow2*
|
||||
```
|
||||
|
||||
**2) Install the virtual machine (virt-install command)**
|
||||
|
||||
a. Create a virtual machine from an ISO image.
|
||||
|
||||
```
|
||||
# virt-install --name client instance name --memory memory memory size --vcpus cpu cores --disk path=disk image path --cdrom=installation media path --network network interface --cdrom=installation media path
|
||||
#Example:
|
||||
$ virt-install --name rhel8 --memory 2048 --vcpus 2 --disk path=./rhel8.qcow2 --cdrom=/media/hollowman/软件/ISO/rhel-8.0-x86_64-linuxprobe.com.iso --network bridge=virbr1
|
||||
```
|
||||
|
||||
b. Create a virtual machine from an existing qcow disk image
|
||||
|
||||
```
|
||||
# virt-install --name client instance name --memory memory memory size --vcpus cpu cores --disk path=disk image path --network network interface --import
|
||||
#Example:
|
||||
$sudo virt-install --name openEuler2109 --memory 2048 --vcpus 2 --disk path=./openEuler-21.09-x86_64.qcow2 --network bridge=virbr1 --import
|
||||
```
|
||||
|
||||
Descriptions of virt-install related options can be viewed with the command.
|
||||
|
||||
```
|
||||
$ virt-install help # The following is a partial excerpt
|
||||
|
||||
General options:
|
||||
-n NAME, --name NAME Client instance name
|
||||
--memory MEMORY The size of the client memory. Example: --memory 1024 (in MiB)
|
||||
--vcpus VCPUS Number of client cpu cores (not larger than host cores). For example:--vcpus 5
|
||||
|
||||
Installation method options:
|
||||
--cdrom CDROM CD-ROM drive installation media
|
||||
--import Build the client from an existing disk image
|
||||
|
||||
OS options:
|
||||
--os-variant OS_VARIANT Specify the operating system type. For example: rhl8.0, you can see all OS types with the 'osinfo-query' command
|
||||
|
||||
Device options:
|
||||
--disk DISK Specifies various options for storage. For example: --disk size=10 (creates a 10GiB image in the default location)
|
||||
-w NETWORK, --network NETWORK Configure the client network interface. For example: --network bridge=mybr0
|
||||
|
||||
```
|
||||
|
||||
### V. Problems found in the virtual machine management process to deal with
|
||||
|
||||
> 1. qcow2 image occupies too much space
|
||||
|
||||
If you create a 40G disk image through virt-manager GUI, you find that the storage space on the host is 40G, such a large footprint, is it OCD? We can deal with it by command compression.
|
||||
|
||||
As follows, we check the disk image information created by virt-manager.
|
||||
|
||||
```
|
||||
$ qemu-img info rhel8.qcow2 #Viewing disk image information
|
||||
image: rhel8.qcow2
|
||||
file format: qcow2
|
||||
virtual size: 40 GiB (42949672960 bytes) #Virtual Disk Size
|
||||
disk size: 196 KiB #This is the actual space occupied by the mirror
|
||||
cluster_size: 65536
|
||||
Format specific information:
|
||||
compat: 1.1
|
||||
lazy refcounts: false
|
||||
refcount bits: 16
|
||||
corrupt: false
|
||||
|
||||
$ ll -h rhel8.qcow2 #View the storage space of the image on the host system (this is the disk created via virt-manager)
|
||||
-rwxrwxrwx 1 hollowman hollowman 40G November 24 13:48 rhel8.qcow2*
|
||||
|
||||
```
|
||||
|
||||
Enter the compression command.
|
||||
|
||||
```
|
||||
$ qemu-img convert -O qcow2 rhel8.qcow2 rhel8_new.qcow2
|
||||
$ ll -h rhel8_new.qcow2
|
||||
-rwxrwxrwx 1 hollowman hollowman 196K November 24 13:52 rhel8_new.qcow2*
|
||||
```
|
||||
You can find that the storage space has changed back to 196K.
|
||||
|
||||
> 2. Mount the qcow2 disk image on the host system
|
||||
|
||||
qcow2 is essentially a virtual disk image, so the contents of this disk image partition can be read on the host system by mounting the disk image partition (if it is a virtual machine disk, you need to operate with the virtual machine turned off).
|
||||
|
||||
|
||||
> 3. When creating a virtual machine, there is a prompt that the 'libvirt-qemu' user does not have permission to search for directory-related records, and the creation is unsuccessful.
|
||||
|
||||
Check and modify the configuration file `/etc/libvirt/qemu.conf`, find the line `# user = "root"` and remove the comment, restart the libvirtd service
|
||||
|
||||
```
|
||||
$ sudo pluma /etc/libvirt/qemu.conf #Modify the following line
|
||||
user = "root"
|
||||
|
||||
$ systemctl restart libvirtd
|
||||
|
||||
```
|
||||
> 4. When opening the virtual machine, "Error connecting to the graphics console: Error opening SPICE console: Namespace SpiceClientGtk not available" appears
|
||||
|
||||
```
|
||||
sudo apt install spice-client-gtk gir1.2-spiceclientgtk-3.0
|
||||
```
|
||||
|
||||
|
After Width: | Height: | Size: 74 KiB |
|
After Width: | Height: | Size: 69 KiB |
|
After Width: | Height: | Size: 70 KiB |
|
After Width: | Height: | Size: 56 KiB |
|
After Width: | Height: | Size: 64 KiB |
|
After Width: | Height: | Size: 76 KiB |
|
After Width: | Height: | Size: 42 KiB |
|
After Width: | Height: | Size: 23 KiB |
|
After Width: | Height: | Size: 28 KiB |
|
|
@ -0,0 +1,181 @@
|
|||
# <center>the principle is not the same snap</center>
|
||||
#### <center>Author: OK</center>
|
||||
#### <center>2022-04-22 23:36:00</center>
|
||||
|
||||
|
||||
**Foreword**
|
||||
|
||||
Both snap and flatpak are the next generation of package management technology across Linux distributions. We briefly introduced the principle of flatpak in the last article (Portal), and today we will continue with a brief introduction to the security mechanism of snap.
|
||||
|
||||
|
||||
### Introduction
|
||||
|
||||
snap is a new generation of Linux package management tool proposed by Canoncial, dedicated to unify the package format on all Linux distributions, so that "once packaged, used everywhere". Currently snap is available on several Linux distributions, including Ubuntu, Fedora, Mint, etc. First, let's understand the various terms related to snap.
|
||||
|
||||
#### snap
|
||||
|
||||
A new generation of package management technology across Linux distributions, supporting all major Linux distributions, ensuring user data security through the Linux kernel security mechanism, completely solving package dependency-related problems, and greatly simplifying the application software packaging process. snap is also a command-line tool for installing and managing snap packages.
|
||||
#### snapd
|
||||
|
||||
Manage the backend services of the snap package.
|
||||
#### kernel snap
|
||||
|
||||
Kernel packaged in snap format, containing kernel images and kernel modules.
|
||||
#### OS snap
|
||||
|
||||
The rootfs, repackaged using the snap format, contain the basic resources to run and manage snap, and when you first install snap, OS snap is installed first.
|
||||
|
||||
#### snapcraft
|
||||
|
||||
A collection of packaging tools to package software into snap format.
|
||||
|
||||
#### snappy
|
||||
|
||||
This name has been deprecated and is now known as Ubuntu Core, which is Ubuntu's full-snap operating system, as opposed to classic Ubuntu, which is traditionally based on deb packages.
|
||||
|
||||
|
||||
### Security Policy
|
||||
|
||||
snap applications run in a sandbox. The system implements its security features by limiting the application's access to resources through a number of mechanisms, such as sandboxing and snap file system implemented through the configuration of kernel security mechanisms AppArmor, Seccomp, etc. Developers do not need to know much about the details of system security mechanisms. The following is a brief description of some of the security policies used by snap.
|
||||
#### Sandbox
|
||||
|
||||
Linux Sandbox is a method of process access control based on a number of security mechanisms supported in the kernel. A process is usually placed in a strictly restricted state by assigning it a random uid, placing it in a chroot environment, and configuring Capability for the process uid. snap applications use this method to run in the sandbox environment assigned to them by the system.
|
||||
#### security policy ID
|
||||
|
||||
Each snap application command has a unique security policy ID, which the system binds to the command, thus allowing different security policies to be configured for different programs within the same snap package. As a marker for the system to identify the command, when the program is installed and run, the system will allocate resources to it according to its Security Policy ID. Communication control between snap applications running in the sandbox is also configured by this ID.
|
||||
|
||||
The security policy ID of a snap application is named snap.name.command
|
||||
For example, the security policy ID of the hello application is snap.hello.hello
|
||||
#### snap file system
|
||||
|
||||
The snap file system is divided into areas with read-only and read-write permissions, and each snap application has its own unique restricted file directory, as shown in the following figure.
|
||||
|
||||
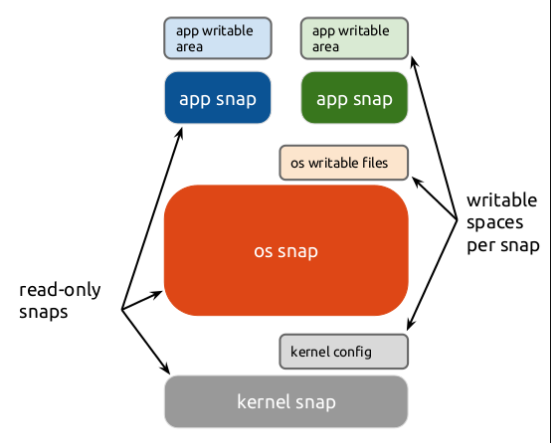
|
||||
|
||||
|
||||
File access permissions for an application can be viewed as follows.
|
||||
|
||||
$ snap install hello
|
||||
hello 2.10 from 'canonical' installed
|
||||
$ snap run --shell hello.hello
|
||||
|
||||
|
||||
$ env | grep SNAP
|
||||
SNAP_USER_COMMON=/home/kylin/snap/hello/common
|
||||
# Writable directory for all versions of the application for a single user
|
||||
|
||||
SNAP_LIBRARY_PATH=/var/lib/snapd/lib/gl:/var/lib/snapd/void
|
||||
# Add to the directory of LD_LABRARY_PATH
|
||||
|
||||
SNAP_COMMON=/var/snap/hello/common
|
||||
# Writable directory for all versions of applications for all users
|
||||
|
||||
SNAP_USER_DATA=/home/kylin/snap/hello/20
|
||||
# Writable directory for single-user specified versions of applications
|
||||
|
||||
SNAP_DATA=/var/snap/hello/20
|
||||
# Writeable directory for all user-specified versions of the application
|
||||
|
||||
As can be seen, the directories to which a snap application has write access are extremely limited, and each snap application has its own separate writable directory. snap file system's configuration of permissions for snap application-related directories illustrates that this approach achieves isolation between application and application, and application and system.
|
||||
|
||||
At the same time, this approach provides good support for upgrade and rollback of snap applications. To upgrade, you only need to copy the relevant directory of the determined version to the corresponding directory of the higher version, and to rollback, you only need to delete the directory of the higher version.
|
||||
#### AppArmor
|
||||
|
||||
AppArmor is a mandatory access control system that provides control at the kernel level over the resources that processes can access. When a snap application is installed, the system generates its own AppArmor-specific configuration file for each of these commands. The kernel's Capability limits on executable programs can also be configured through Aparmor. When executing a command in an application, the AppArmor mechanism ensures that the command does not override access rights. As a security mechanism in the kernel, AppArmor is also supported in ubuntu classic. Unlike classic, however, the snap system has much stricter access control, basically "only the least privilege required for program execution".
|
||||
#### Seccomp
|
||||
|
||||
Seccomp is a kernel interface access filter through which a snap application accesses the kernel interface. Seccomp has a similar role in the snap system to AppArmor, in that it controls the application's access to system resources.
|
||||
|
||||
Snap interface calls
|
||||
|
||||
snap applications are strictly limited to the security policy described above, but communication between snap applications is also required, for example, a hardware driver as a snap application must provide interfaces and services for applications using this hardware. The following is a brief explanation of the communication mechanism between snap applications.
|
||||
#### Default Security Policy
|
||||
|
||||
In the absence of special configuration, snap applications use the default security policy, which contains the default directory access control in the snap file system mentioned earlier, as well as the following partial policies.
|
||||
|
||||
- Read-only permissions for the snap application installation directory.
|
||||
|
||||
- Read and write access to shared memory (ie. /dev/shm/snap.SNAP_NAME.*)
|
||||
|
||||
- Permissions for different processes of the same application to send signal to each other
|
||||
#### Installation mode
|
||||
|
||||
snap provides different resource access control through different installation modes。
|
||||
1) Devmode
|
||||
|
||||
devmode is the development mode. Use the following command to install the application in this mode.
|
||||
|
||||
$ snap install hello --devmode
|
||||
$ snap list
|
||||
Name Version Rev Developer Notes
|
||||
core 16-2.26.9 2381 canonical -
|
||||
hello 2.10 20 canonical devmode
|
||||
pc 16.04-0.8 9 canonical -
|
||||
pc-kernel 4.4.0-83.106 68 canonical -
|
||||
|
||||
This mode provides full access to the application, but logs the program's overstepping in the log.
|
||||
|
||||
Under devmode, the snap application can only access files under /snap/.
|
||||
2) Classic
|
||||
|
||||
This mode will remove all access restrictions and no overstepping will be recorded in the logs.
|
||||
|
||||
In classic mode, the snap application can access the files under '/'.
|
||||
#### Interfaces
|
||||
|
||||
In addition to the resources provided by the default security policy, snap applications do not have access to other system resources. If a snap application needs to use system resources or resources provided by other applications, it needs to configure interfaces through the interfaces mechanism. interfaces are divided into two types of interfaces, slot (service provider) and plug (service user).
|
||||
|
||||
The snap application access to restricted resources is illustrated as follows.
|
||||
|
||||
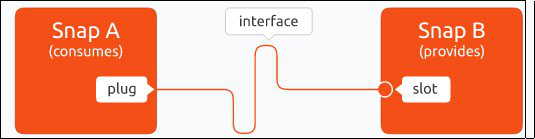
|
||||
|
||||
Note: The operating system also exists as a snap application in the snap system.
|
||||
As shown in the figure, snap applications can be accessed from each other by configuring the plug and slot of the snap application.
|
||||
|
||||
Check for existing bugs and slots on the system:
|
||||
|
||||
$ snap interfaces
|
||||
Slot Plug
|
||||
:account-control -
|
||||
:alsa -
|
||||
:autopilot-introspection -
|
||||
:bluetooth-control -
|
||||
:browser-support -
|
||||
:camera -
|
||||
:classic-support classic
|
||||
:core-support core:core-support-plug
|
||||
.........
|
||||
The following is an example to illustrate the use of plug and slot.
|
||||
|
||||
name: blue
|
||||
...
|
||||
apps:
|
||||
blue:
|
||||
command: bin/blue
|
||||
slots: 【bluez】
|
||||
|
||||
The above file can be used as a snap package packaging control file for a Bluetooth device driver. When this application is installed, it will be assigned the security policy ID snap.blue.blue and contain the rule: create a bluez slot for blue when it starts.
|
||||
|
||||
To use the functionality provided by this slot in other applications, the package control file looks like this.
|
||||
|
||||
name: blue-client
|
||||
...
|
||||
apps:
|
||||
blue-client:
|
||||
command: bin/blue-client
|
||||
plugs: 【bluez】
|
||||
|
||||
Similarly, when this application is installed, the system will assign the security policy ID to snap.blue-client.blue-client and include the rule: allow this application to communicate with snap.blue.blue. Also, the security rule providing the slot will be rewritten to read: snap.blue.blue allows snap.blue-client.blue-client to communicate with it.
|
||||
|
||||
The following diagram illustrates the mutual communication between snap applications and applications under strict separation constraints.
|
||||
|
||||
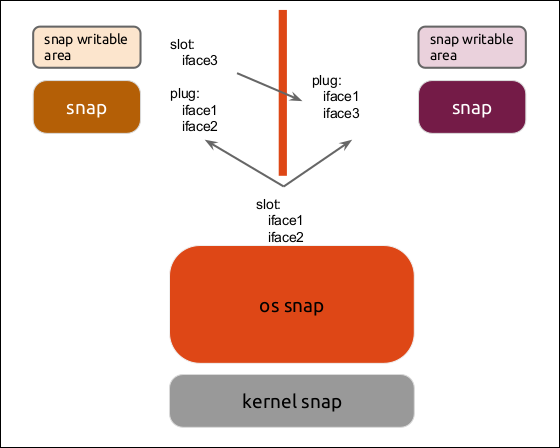
|
||||
|
||||
|
||||
|
||||
The snap system consists of snap applications, including the system and kernel, in the form of snap packages. Each snap package provides services to each other through interfaces to accomplish cooperative work, while each application does not lose its independence.
|
||||
|
||||
|
||||
### Summary
|
||||
|
||||
The snap system provides a robust security system. Compared to traditional linux distributions, applications in snap systems are more independent and secure, while the configuration of snap application permissions is simpler. In the growing demand of embedded and IoT with the increasingly serious system security situation, snap system shows outstanding advantages over traditional linux distributions.
|
||||